[ad_1]
Take into consideration how a lot of the world depends on the web. The federal government, army, academia, well being care trade, and personal trade not solely accumulate, course of, and retailer unprecedented quantities of information in our on-line world — additionally they depend on essential infrastructure techniques in our on-line world to carry out operations and ship providers.
An assault on this infrastructure couldn’t solely threaten buyer knowledge or a enterprise’s backside line — it might additionally threaten a nation’s safety, economic system, and public security and well being.
Contemplating its significance, we’ve compiled this final information on cybersecurity. Under, we’ll discuss what cybersecurity is strictly, the right way to shield your techniques and knowledge from assaults, and what assets to observe to remain up-to-date with rising traits and know-how associated to cybersecurity.
Good cybersecurity entails a number of layers of safety throughout the info, gadgets, packages, networks, and techniques of an enterprise. A mix of know-how and greatest practices can present an efficient protection towards the frequently evolving and rising threats of our on-line world.
These threats embody phishing, malware, ransomware, code injections, and extra. The impression can differ relying on the scope of the assault. A cyber assault may consequence within the attacker making unauthorized purchases with a person’s bank card information, or erasing a complete system after injecting malware into a company’s code base.
Whereas even the perfect cybersecurity can’t defend towards each sort or occasion of assault, it could assist to attenuate the dangers and impression of such assaults.
Varieties of Cybersecurity
Cybersecurity is a broad time period that may be damaged down into extra particular subcategories. Under we’ll stroll by means of 5 main varieties of cybersecurity.
Software Safety
Software safety, also referred to as AppSec, is the follow of growing, including, and testing security measures inside internet purposes in an effort to shield them towards assaults. Vulnerabilities, safety misconfigurations, and design flaws may be exploited and end in malicious code injections, delicate knowledge publicity, system compromise, and different unfavourable impacts. HubSpot’s Content material Hub gives a free internet utility firewall (WAF) that may shield your web site and content material from malicious assaults.
AppSec is among the most necessary varieties of cybersecurity as a result of the appliance layer is essentially the most susceptible. In accordance with Imperva analysis, almost half of information breaches over the previous a number of years originated on the internet utility layer.
Cloud Safety
Cloud safety is a comparatively latest sort of cybersecurity. It’s the follow of defending cloud computing environments in addition to purposes working in and knowledge saved within the cloud.
Since cloud suppliers host third-party purposes, providers, and knowledge on their servers, they’ve safety protocols and options in place — however purchasers are additionally partially accountable and anticipated to configure their cloud service correctly and use it safely.
Vital Infrastructure Safety
Vital infrastructure safety is the follow of defending the essential infrastructure of a area or nation. This infrastructure consists of each bodily safety and cyber networks, techniques, and belongings that present bodily and financial safety or public well being and security. Consider a area’s electrical energy grid, hospitals, visitors lights, and water techniques as examples.
A lot of this infrastructure is digital or depends on the web in a roundabout way to operate. It’s subsequently prone to cyber assaults and have to be secured.
Web of Issues (IoT) safety
Web of Issues safety, or IoT safety, is the follow of defending nearly any machine that connects to the web and might talk with the community independently of human motion. This consists of child screens, printers, safety cameras, movement sensors, and a billion different gadgets in addition to the networks they’re related to.
Since IoT gadgets accumulate and retailer private data, like an individual’s title, age, location, and well being knowledge, they may also help malicious actors steal folks’s identities and have to be secured towards unauthorized entry and different threats.
Community Safety
Community safety is the follow of defending laptop networks and knowledge towards exterior and inner threats. Identification and entry controls like firewalls, digital personal networks, and two-factor authentication may also help.
Community safety is usually damaged down into three classes: bodily, technical, and administrative. Every of some of these community safety is about guaranteeing solely the best folks have entry to community elements (like routers), knowledge that’s saved in or transferred by the community, and the infrastructure of the community itself.
Cybersecurity Phrases to Know
Cybersecurity is a really intimidating matter, not not like cryptocurrency and synthetic intelligence. It may be arduous to grasp, and, frankly, it sounds form of ominous and sophisticated.
However worry not. We’re right here to interrupt this matter down into digestible items that you may rebuild into your individual cybersecurity technique. Bookmark this submit to maintain this helpful glossary at your fingertips.
Right here’s a complete listing of basic cybersecurity phrases you need to know.
Authentication
Authentication is the method of verifying who you’re. Your passwords authenticate that you simply actually are the one who ought to have the corresponding username. Whenever you present your ID (e.g., driver’s license, and many others), the truth that your image usually seems such as you is a manner of authenticating that the title, age, and handle on the ID belong to you. Many organizations use two-factor authentication, which we cowl later.
Backup
A backup refers back to the technique of transferring necessary knowledge to a safe location like a cloud storage system or an exterior arduous drive. Backups allow you to recuperate your techniques to a wholesome state in case of a cyber assault or system crash.
Conduct Monitoring
Conduct monitoring is the method of observing the actions of customers and gadgets in your community to acknowledge any potential safety occasions earlier than they happen. Actions should not solely be noticed but in addition measured towards baselines of regular conduct, traits, and organizational insurance policies and guidelines.
For instance, you may monitor and monitor when customers log in and log off, in the event that they request entry to delicate belongings, and what web sites they go to. Then say a person tries to log in at an uncommon time, just like the nighttime. In that case, you may determine that as uncommon conduct, examine it as a possible safety occasion, and finally block that log in try if you happen to suspect an assault.
Bot
A bot, quick for robotic, is an utility or script designed to carry out automated and repetitive duties. Some bots have official functions, like chatbots that reply generally requested questions on a web site. Others are used for malicious functions, like sending spam emails or conducting DDoS assaults. As bots develop into extra refined, it will get tougher to inform the distinction between good bots and dangerous bots and even bots from human customers. That’s why bots pose an ever-growing risk to many people and organizations.
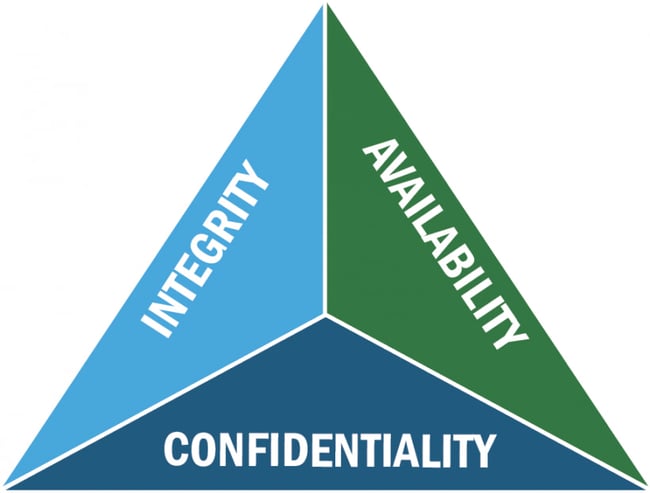
CIA Triad
The CIA triad is a mannequin that can be utilized to develop or consider a company’s cybersecurity techniques and insurance policies.
The CIA triad refers to confidentiality, integrity, and availability. In follow, this mannequin ensures knowledge is disclosed solely to approved customers, stays correct and reliable all through its lifecycle, and may be accessed by approved customers when wanted despite software program failures, human error, and different threats.
Knowledge Breach
An information breach refers back to the second a hacker features unauthorized entry or entry to an organization’s or a person’s knowledge.
Digital Certificates
A digital certificates, also referred to as an id certificates or public key certificates, is a kind of passcode used to securely change knowledge over the web. It’s primarily a digital file embedded in a tool or piece of {hardware} that gives authentication when it sends and receives knowledge to and from one other machine or server.
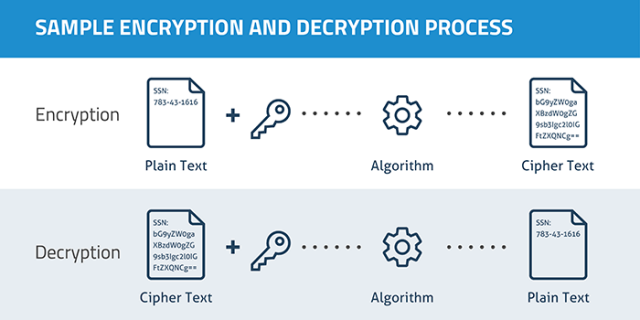
Encryption
Encryption is the follow of utilizing codes and ciphers to encrypt knowledge. When knowledge is encrypted, a pc makes use of a key to show the info into unintelligible gibberish. Solely a recipient with the proper key is ready to decrypt the info. If an attacker will get entry to strongly encrypted knowledge however doesn’t have the important thing, they aren’t in a position to see the unencrypted model.
HTTP and HTTPS
Hypertext Switch Protocol (HTTP) is how internet browsers talk. You’ll most likely see an http:// or https:// in entrance of the web sites you go to. HTTP and HTTPS are the identical, besides HTTPS encrypts all knowledge despatched between you and the online server — therefore the “S” for safety. Right this moment, almost all web sites use HTTPS to enhance the privateness of your knowledge just like the free SSL supplied by the free Content material Hub.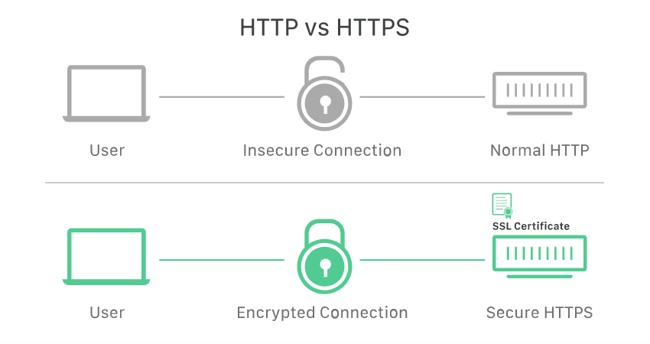
Vulnerability
A vulnerability is a spot of weak point {that a} hacker may exploit when launching a cyber assault. Vulnerabilities is perhaps software program bugs that have to be patched, or a password reset course of that may be triggered by unauthorized folks. Defensive cybersecurity measures (like those we discuss later) assist guarantee knowledge is protected by placing layers of protections between attackers and the issues they’re attempting to do or entry.
A cyber assault is a deliberate and sometimes malicious intent to seize, modify, or erase personal knowledge. Cyber assaults are dedicated by exterior safety hackers and, typically, unintentionally by compromised customers or staff. These cyber assaults are dedicated for a wide range of causes. Some are on the lookout for ransom, whereas some are merely launched for enjoyable.
Under we’ll briefly go over the commonest cyber threats.
1. Password Guessing (Brute Power) Assault
A password guessing (or “credential stuffing”) assault is when an attacker frequently makes an attempt to guess usernames and passwords. This assault will typically use recognized username and password mixtures from previous knowledge breaches.
An attacker is profitable when folks use weak passwords or use the password between totally different techniques (e.g., when your Fb and Twitter password are the identical, and many others). Your greatest protection towards this type of assault is utilizing robust passwords and avoiding utilizing the identical password in a number of locations in addition to utilizing two issue authentication, as we discuss later.)
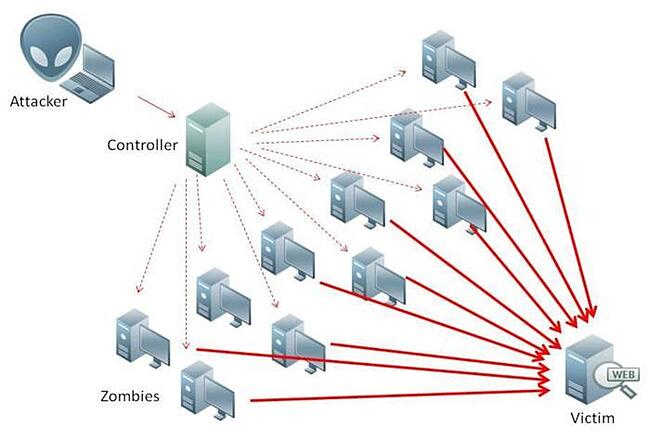
2. Distributed Denial of Service (DDoS) Assault
A distributed denial of service (DDoS) assault is when a hacker floods a community or system with a ton of exercise (akin to messages, requests, or internet visitors) in an effort to paralyze it.
That is sometimes carried out utilizing botnets, that are teams of internet-connected gadgets (e.g., laptops, mild bulbs, recreation consoles, servers, and many others) contaminated by viruses that permit a hacker to harness them into performing many sorts of assaults.
3. Malware Assault
Malware refers to all varieties of malicious software program utilized by hackers to infiltrate computer systems and networks and accumulate prone personal knowledge. Varieties of malware embody:
Keyloggers, which monitor every little thing an individual varieties on their keyboard. Keyloggers are often used to seize passwords and different personal data, akin to social safety numbers.
Ransomware, which encrypts knowledge and holds it hostage, forcing customers to pay a ransom in an effort to unlock and regain entry to their knowledge.
Spy ware, which screens and “spies” on person exercise on behalf of a hacker.
Moreover, malware may be delivered through:
Trojan horses, which infect computer systems by means of a seemingly benign entry level, typically disguised as a official utility or different piece of software program.
Viruses, which corrupt, erase, modify, or seize knowledge and, at instances, bodily harm computer systems. Viruses can unfold from laptop to laptop, together with when they’re unintentionally put in by compromised customers.
Worms, that are designed to self-replicate and autonomously unfold by means of all related computer systems which can be prone to the identical vulnerabilities. .
4. Phishing Assault
A phishing assault is when hackers attempt to trick folks into doing one thing. Phishing scams may be delivered by means of a seemingly official obtain, hyperlink, or message.
It’s a quite common sort of cyber assault — 57% of respondents in a third-party survey stated their group skilled a profitable phishing assault in 2020, up from 55% in 2019. And the impression of profitable phishing assaults vary from lack of knowledge to monetary loss.
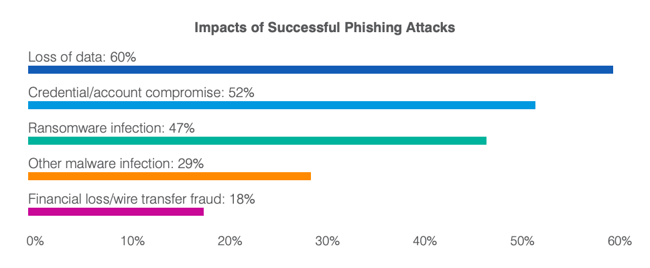
Phishing is usually carried out over electronic mail or by means of a faux web site; it’s also referred to as spoofing. Moreover, spear phishing refers to when a hacker focuses on attacking a selected individual or firm, akin to stealing their id, as a substitute of making extra general-purpose spams.
5. Man-in-the-Center (MitM) Assault
A Man-in-the-Center (MitM) assault is when an attacker intercepts communications or transactions between two events and inserts themselves within the center. The attacker can then intercept, manipulate, and steal knowledge earlier than it reaches its official vacation spot. For instance, say a customer is utilizing a tool on public WiFi that hasn’t been secured correctly, or in any respect. An attacker might exploit this vulnerability and insert themselves between the customer’s machine and the community to intercept login credentials, fee card data, and extra.
Such a cyber assault is so profitable as a result of the sufferer has no concept that there’s a “man within the center.” It simply looks as if they’re searching the online, logging into their financial institution app, and so forth.
%20Attack-p-500.jpeg?width=650&name=605cab5ff8f386ea033ae16c_Man-in-the-Middle)%20Attack-p-500.jpeg)
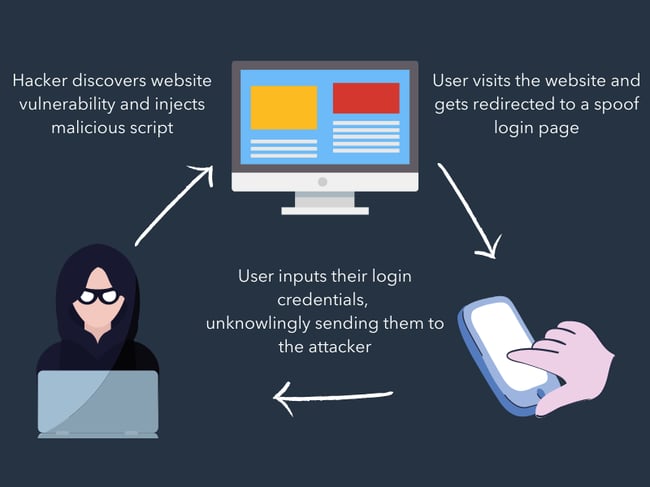
6. Cross Web site Scripting Assault
A cross web site scripting assault, or XSS assault, is when an attacker injects malicious code into an in any other case official web site or utility in an effort to execute that malicious code in one other person’s internet browser.
As a result of that browser thinks the code is coming from a trusted supply, it can execute the code and ahead data to the attacker. This data is perhaps a session token or cookie, login credentials, or different private knowledge.
This is an illustrated instance of an XSS assault:
Picture Supply
7. SQL Injection Assault
An SQL injection assault is when an attacker submits malicious code by means of an unprotected type or search field in an effort to achieve the power to view and modify the web site’s database. The attacker may use SQL, quick for Structured Question Language, to make new accounts in your web site, add unauthorized hyperlinks and content material, and edit or delete knowledge.
This can be a frequent WordPress safety challenge since SQL is the popular language on WordPress for database administration.
Cybersecurity Greatest Practices: The right way to Safe Your Knowledge
Cybersecurity can’t be boiled down right into a 1-2-3-step course of. Securing your knowledge entails a mixture of greatest practices and defensive cybersecurity methods. Dedicating time and assets to each is the easiest way to safe your — and your clients’ — knowledge.
Defensive Cybersecurity Options
All companies ought to spend money on preventative cybersecurity options. Implementing these techniques and adopting good cybersecurity habits (which we focus on subsequent) will shield your community and computer systems from outdoors threats.
Right here’s a listing of 5 defensive cybersecurity techniques and software program choices that may stop cyber assaults — and the inevitable headache that follows. Take into account combining these options to cowl all of your digital bases.
Antivirus Software program
Antivirus software program is the digital equal of taking that vitamin C increase throughout flu season. It’s a preventative measure that screens for bugs. The job of antivirus software program is to detect viruses in your laptop and take away them, very like vitamin C does when dangerous issues enter your immune system. (Spoken like a real medical skilled …) Antivirus software program additionally alerts you to probably unsafe internet pages and software program.
Be taught extra: McAfee, Norton. or Panda (without spending a dime)
Firewall
A firewall is a digital wall that retains malicious customers and software program out of your laptop. It makes use of a filter that assesses the security and legitimacy of every little thing that wishes to enter your laptop; it’s like an invisible choose that sits between you and the web. Firewalls are each software program and hardware-based.
Be taught extra: McAfee LiveSafe or Kaspersky Web Safety
Put money into Risk Detection and Prevention
Whether or not you are utilizing the Content material Hub or a standard web site internet hosting service like WordPress, it is important to combine a device to scan and detect threats. Most content material administration techniques will embody a malware scanning and risk detection characteristic inside the platform. However if you happen to use platforms like WordPress, you need to spend money on a safety scanner.
Single Signal-On (SSO)
Single sign-on (SSO) is a centralized authentication service by means of which one login is used to entry a complete platform of accounts and software program. Should you’ve ever used your Google account to enroll or into an account, you’ve used SSO. Enterprises and firms use SSO to permit staff entry to inner purposes that include proprietary knowledge.
Be taught extra: Okta or LastPass
Two-Issue Authentication (2FA)
Two-factor authentication (2FA) is a login course of that requires a username or pin quantity and entry to an exterior machine or account, akin to an electronic mail handle, telephone quantity, or safety software program. 2FA requires customers to substantiate their id by means of each and, due to that, is much safer than single issue authentication.
Be taught extra: Duo
Digital Personal Community (VPN)
A digital personal community (VPN) creates a “tunnel” by means of which your knowledge travels when coming into and exiting an internet server. That tunnel encrypts and protects your knowledge in order that it could’t be learn (or spied on) by hackers or malicious software program. Whereas safe VPNs shield towards spy ware, they’ll’t stop viruses from coming into your laptop by means of seemingly official channels, like phishing or perhaps a faux VPN hyperlink. Due to this, VPNs ought to be mixed with different defensive cybersecurity measures in an effort to shield your knowledge.
Be taught extra: Cisco’s AnyConnect or Palo Alto Networks’ GlobalProtect
Cybersecurity Suggestions for Enterprise
Defensive cybersecurity options gained’t work until you do. To make sure what you are promoting and buyer knowledge is protected, undertake these good cybersecurity habits throughout your group.
Require robust credentials.
Require each your staff and customers (if relevant) to create robust passwords. This may be carried out by implementing a personality minimal in addition to requiring a mixture of higher and lowercase letters, numbers, and symbols. Extra sophisticated passwords are tougher to guess by each people and bots. Additionally, require that passwords be modified commonly.

Management and monitor worker exercise.
Inside what you are promoting, solely give entry to necessary knowledge to approved staff who want it for his or her job. Prohibit knowledge from sharing outdoors the group, require permission for exterior software program downloads, and encourage staff to lock their computer systems and accounts every time not in use.
Know your community.
With the rise of the Web of Issues, IoT gadgets are popping up on firm networks like loopy. These gadgets, which aren’t beneath firm administration, can introduce threat as they’re typically unsecured and run susceptible software program that may be exploited by hackers and supply a direct pathway into an inner community.
“Be sure to have visibility into all of the IoT gadgets in your community. Every part in your company community ought to be recognized, correctly categorized, and managed. By realizing what gadgets are in your community, controlling how they connect with it, and monitoring them for suspicious actions, you will drastically scale back the panorama attackers are taking part in on.” — Nick Duda, Principal Safety Officer at HubSpot
Examine how HubSpot features machine visibility and automates safety administration in this case examine compiled by safety software program ForeScout.
Obtain patches and updates commonly.
Software program distributors commonly launch updates that handle and repair vulnerabilities. Hold your software program protected by updating it on a constant foundation. Take into account configuring your software program to replace robotically so that you always remember.
Make it straightforward for workers to escalate points.
In case your worker comes throughout a phishing electronic mail or compromised internet web page, you wish to know instantly. Arrange a system for receiving these points from staff by dedicating an inbox to those notifications or making a type that individuals can fill out.
Cybersecurity Suggestions for People
Cyber threats can have an effect on you as a person client and web person, too. Undertake these good habits to guard your private knowledge and keep away from cyber assaults.
Combine up your passwords.
Utilizing the identical password for all of your necessary accounts is the digital equal of leaving a spare key beneath your entrance doormat. A latest examine discovered that over 80% of information breaches have been a results of weak or stolen passwords. Even when a enterprise or software program account doesn’t require a powerful password, all the time select one which has a mixture of letters, numbers, and symbols and alter it commonly.
Monitor your financial institution accounts and credit score continuously.
Assessment your statements, credit score stories, and different essential knowledge frequently and report any suspicious exercise. Moreover, solely launch your social safety quantity when completely needed.
Be intentional on-line.
Hold an eye fixed out for phishing emails or illegitimate downloads. If a hyperlink or web site seems fishy (ha — get it?), it most likely is. Search for dangerous spelling and grammar, suspicious URLs, and mismatched electronic mail addresses. Lastly, obtain antivirus and safety software program to provide you with a warning of potential and recognized malware sources.
Again up your knowledge commonly.
This behavior is nice for companies and people to grasp — knowledge may be compromised for each events. Take into account backups on each cloud and bodily areas, akin to a tough drive or thumb drive.
Why You Ought to Care About Cybersecurity
In accordance with a report by RiskBased Safety, there have been 3,932 knowledge breaches reported in 2020, which uncovered over 37 billion data. Furthermore, a latest examine discovered that the worldwide common price of an information breach amounted to 3.86 million U.S. {dollars} in 2020. Which means the price of knowledge breaches amounted to roughly 15.2 billion {dollars} final 12 months.
Small to medium-sized companies (SMBs) are particularly in danger. You may see firms like Goal and Sears topping the headlines as prime knowledge breach victims, but it surely’s really SMBs that hackers desire to focus on.
Why? They’ve extra — and extra invaluable — digital belongings than your common client however much less safety than a bigger enterprise-level firm … inserting them proper in a “hackers’ cybersecurity candy spot.”
Safety breaches are irritating and scary for each companies and customers. In a survey by Measure Protocol, roughly 86% of respondents stated that latest privateness breaches within the information had impacted their willingness to share private data to some extent.
However cybersecurity is about extra than simply avoiding a PR nightmare. Investing in cybersecurity builds belief together with your clients. It encourages transparency and reduces friction as clients develop into advocates in your model.
“Everybody has a task in serving to to guard clients’ knowledge. Right here at HubSpot, each worker is empowered to resolve for buyer wants in a protected and safe manner. We wish to harness everybody’s power to supply a platform that clients belief to accurately and safely retailer their knowledge.” — Chris McLellan, HubSpot Chief Safety Officer
Cybersecurity Sources
The assets under will make it easier to study extra about cybersecurity and the right way to higher equip what you are promoting and crew. We additionally suggest testing essentially the most well-liked cybersecurity podcasts and cybersecurity blogs, too.
Nationwide Institute of Requirements and Know-how (NIST)
NIST is a authorities company that promotes excellence in science and trade. It additionally comprises a Cybersecurity division and routinely publishes guides that requirements.
Bookmark: The Pc Safety Useful resource Middle (CSRC) for safety greatest practices, referred to as NIST Particular Publications (SPs).
The Middle for Web Safety (CIS)
CIS is a world, non-profit safety useful resource and IT group used and trusted by consultants within the area.
Bookmark: The CIS High 20 Vital Safety Controls, which is a prioritized set of greatest practices created to cease essentially the most pervasive and harmful threats of in the present day. It was developed by main safety consultants from around the globe and is refined and validated yearly.
Cybrary
Cybrary is a web-based cybersecurity schooling useful resource. It gives principally free, full-length academic movies, certifications, and extra for every kind of cybersecurity subjects and specializations.
Bookmark: The Licensed Info Programs Safety Skilled (CISSP) 2021, which is the latest course for data safety professionals. Incomes this “gold customary” of cybersecurity certifications will set you aside from different data safety professionals.
The Cyber Readiness Institute
The Cyber Readiness Institute is an initiative that convenes enterprise leaders from totally different sectors and areas to share assets and data to finally advance the cyber readiness of small and medium-sized companies.
Bookmark: The Cyber Readiness Program, which is a free, on-line program designed to assist small and medium-sized enterprises safe their knowledge, staff, distributors, and clients towards in the present day’s most typical cyber vulnerabilities.
Signing Off … Securely
Cyber assaults could also be intimidating, however cybersecurity as a subject doesn’t should be. It’s crucial to be ready and armed, particularly if you happen to’re dealing with others’ knowledge. Companies ought to dedicate time and assets to defending their computer systems, servers, networks, and software program and may keep up-to-date with rising tech.
Dealing with knowledge with care solely makes what you are promoting extra reliable and clear — and your clients extra loyal.
Word: Any authorized data on this content material is just not the identical as authorized recommendation, the place an legal professional applies the regulation to your particular circumstances, so we insist that you simply seek the advice of an legal professional if you happen to’d like recommendation in your interpretation of this data or its accuracy. In a nutshell, chances are you’ll not depend on this as authorized recommendation or as a advice of any explicit authorized understanding.
Editor’s notice: This submit was initially revealed in February 2019 and has been up to date for comprehensiveness.
![]()
[ad_2]
Supply hyperlink



