As industrial IoT (IIoT) integration surges, so do safety considerations. Let’s delve into the rising menace panorama and the position of the safety mannequin in fortifying IIoT defences and safeguarding vital infrastructure.
Industrial IoT (IIoT) safety has gained super significance lately. With the rise of IIoT and the growing integration of operational applied sciences (OT) with the web, the necessity for sturdy safety measures has change into paramount. Industrial IoT, sometimes called OT, has remodeled industries throughout the board. The appearance of 5G expertise has made OT property integral to the manufacturing, healthcare, and robotics sectors. These applied sciences have improved operational effectivity and enhanced employee security by lowering accidents in industrial settings.
Previously, OT methods operated in isolation; nonetheless, they’re interconnected as we speak, resulting in extra environment friendly and complicated methods. Distant operations have additionally change into more and more widespread, highlighting the necessity for safe IIoT infrastructure. Whereas IIoT gives quite a few advantages, it additionally introduces safety challenges. Connecting OT methods to the web inherently entails some stage of threat. Current information reviews have highlighted industrial cyberattacks, such because the Ukrainian electrical grid assault and the Saudi oil refinery assault, showcasing the vulnerabilities of elevated connectivity.
Ransomware assaults, specifically, have emerged as a big menace to the manufacturing sector. In 2021 alone, there have been ten profitable ransomware assaults concentrating on manufacturing firms. The implications of such assaults are extreme, disrupting manufacturing, encrypting knowledge, and inflicting monetary losses.
Challenges In India
India is just not immune to those threats. Current assaults on organisations like Oil India, Dr Reddy’s Laboratories, and Tata Energy have underscored the vital nature of IIoT safety. The healthcare sector has not been spared, with establishments like AIIMS falling sufferer to ransomware assaults, paralysing important companies. Probably the most regarding tendencies is the rise of state-sponsored cyberattacks. Nations like China and others are recognized to have interaction in focused campaigns, launching assaults on vital infrastructure worldwide. These assaults have been a relentless menace, with vital incidents reported yearly.
The connectivity dilemma with the growth of IIoT has uncovered safety gaps. That is depicted in Fig. 1.
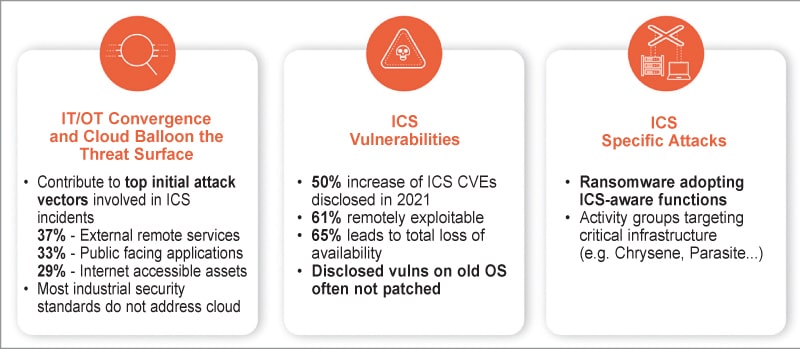 Fig. 1: Safety gaps as a consequence of connectivity dilemma with the growth of IIoT (Credit score: Palo Alto Networks)
Fig. 1: Safety gaps as a consequence of connectivity dilemma with the growth of IIoT (Credit score: Palo Alto Networks)
Many OT methods are externally accessible, with public-facing purposes and web accessibility, making them inclined to assaults. Vulnerabilities in industrial management methods (ICS) have elevated by 50%, with 61% being remotely exploitable. The lack of availability, a vital factor within the CIA triad (confidentiality, integrity, and availability), is a significant concern, with 65% of assaults resulting in downtime. Outdated working methods like Home windows XP and Home windows 7 pose further dangers. Many organisations nonetheless use these unsupported methods, making them straightforward targets for exploitation. Moreover, ransomware assaults concentrating on particular industries have change into a big menace.
 Fig. 2: A number of assault vectors persist regardless of the advances in cybersecurity (Credit score: Palo Alto Networks)
Fig. 2: A number of assault vectors persist regardless of the advances in cybersecurity (Credit score: Palo Alto Networks)
As we proceed to embrace the potential of Industrial IoT, it’s essential to handle the safety challenges that include it. The convergence of OT and IT methods calls for a complete method to cybersecurity. Organisations should prioritise securing their IIoT infrastructure to guard towards potential threats and make sure the uninterrupted operation of vital methods. On this period of connectivity, safety is just not an possibility however a necessity. With vigilance, training, and sturdy cybersecurity measures, we are able to safeguard our industrial IoT property and pave the way in which for a safer and affluent future. As organisations worldwide embrace the alternatives introduced by digital transformation, they need to even be conscious about the dangers that come hand in hand.
 Fig. 3: Menace actors of IIOT (Credit score: Palo Alto Networks)
Fig. 3: Menace actors of IIOT (Credit score: Palo Alto Networks)
Notable industrial cyberattacks and the rising menace panorama in IIoTIn the world of Industrial IoT (IIoT), the potential for catastrophic cyberattacks can’t be underestimated. Listed below are some examples that spotlight the devastating penalties of such assaults:
• The Ukraine energy grid assault. Initiated by a spear-phishing e-mail concentrating on a high-profile particular person, this assault compromised each IT and OT methods, culminating in a community takeover. In simply six hours, 230,000 folks confronted a devastating energy grid shutdown amid freezing temperatures.
• Saudi oil refinery assaults. Focused vital infrastructure in oil and gasoline, nuclear, and manufacturing sectors, posing a grave menace to nationwide safety and worldwide stability.
• Norsk hydro ransomware assaults. Inflicting disruptions in aluminium manufacturing throughout roughly 170 vegetation, these assaults led to vital monetary losses, highlighting the vulnerability of vital industrial infrastructure to cyber threats.
• Colonial pipeline hack. Leading to widespread gasoline and gasoline shortages, this cyberattack disrupted the essential power provide chain, resulting in gasoline shortages at gasoline stations, and underscoring the vulnerability of vital infrastructure to cyber threats, thereby elevating considerations about nationwide safety and resilience.
Nevertheless, new assaults are rising day-after-day. A 2021 report indicated 10 profitable ransomware assaults on the manufacturing phase. The potential loss is staggering, contemplating the encryption of information and shutdown of machines. Because the IIoT panorama expands, so does the menace panorama. The teachings realized ought to function a clarion name for heightened vigilance, rigorous coaching, and stringent safety protocols to guard towards future cyber onslaughts.
The altering face of threats
WHERE IS THE REST OF THIS ARTICLE’S CONTENT?
That is PREMIUM content material, which implies that solely
REGISTERED customers of our web site can learn it, by logging in.
In case you ARE a registered person, CLICK HERE to login.
Else, CLICK HERE to register for FREE!
[ad_2]
Supply hyperlink






